
Safewhere Identify 5.17
We are happy to announce the release of Safewhere Identify 5.17. In this topic, you will find the release notes for all new features and bug fixes in version 5.17, as well as any breaking changes when upgrading from previous versions.
New features and improvements
Safewhere Identify
Identify configurator
Identify Admin redeployment
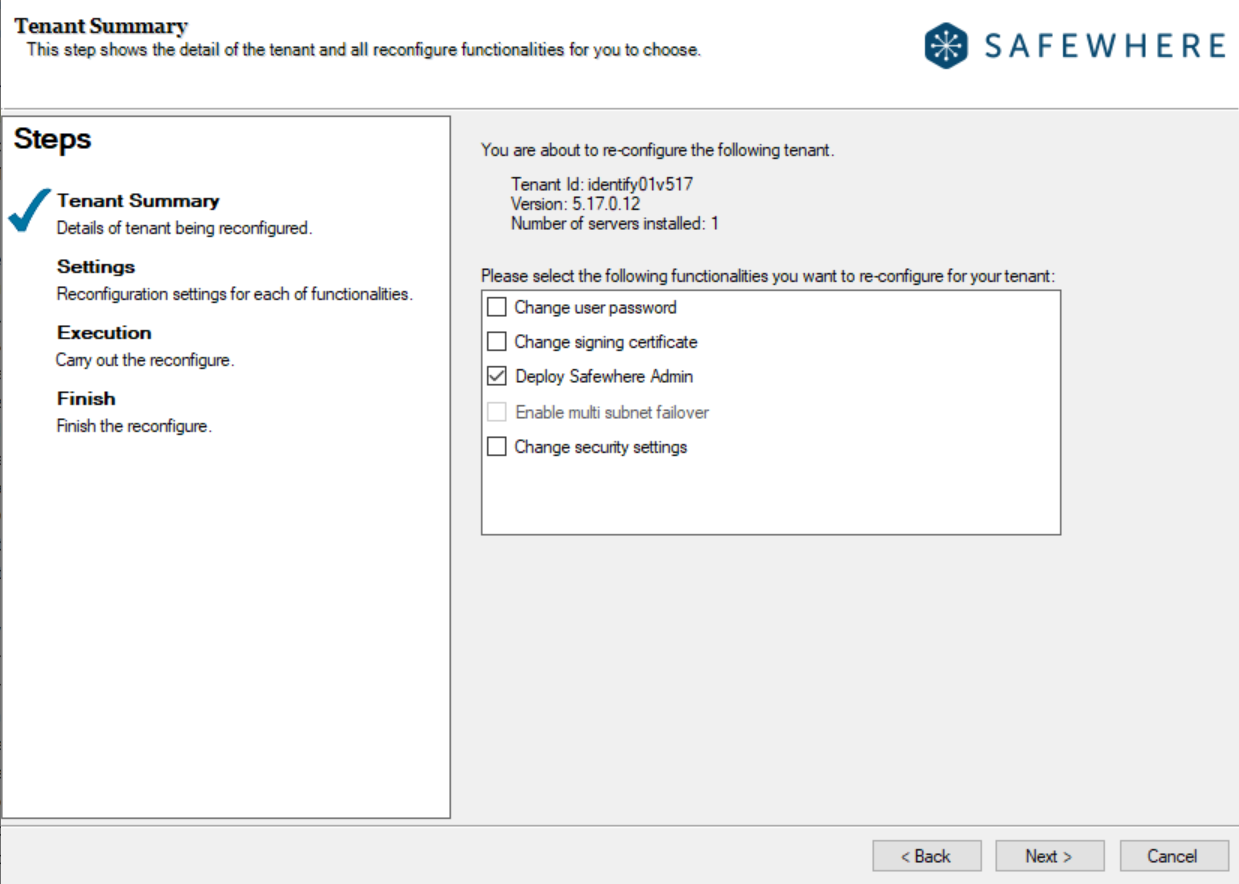
Previously, if the Identify Configurator successfully upgraded an Identify tenant but failed to upgrade its Admin portal (for reasons such as the W3SVC being stopped), users had no alternative but to manually redeploy the Admin portal. In this version, should such a situation occur, a message will appear at the final step, directing you to use the Reconfigure feature to redeploy the failed-to-upgrade Admin portal.

After resolving the issues causing the upgrade failure, use the Reconfigure feature and select Deploy Safewhere Admin for redeployment:
Tip: In case of errors during the Mass Upgrade process, refer to the error report CSV file located at C:\identifylogs to determine which tenants failed to upgrade.
Speed up tenant upgrade
Previously, the “Stopping the application pool” step for the application pool hosting the Admin portal required 30 seconds to complete, regardless of the actual pool status. This resulted in a consistent 30-second delay for each tenant upgrade.
In this version, we have improved the pool status detection mechanism. It now checks the status every 5 seconds, up to 6 times. If the application pool status is confirmed as stopped, the Identify Configurator immediately proceeds to the next step. In the best-case scenario, this improvement can save up to 25 seconds per upgrade.

Data import after renaming the “admin” user
Previously, changing the default administrator account name in an Identify tenant from “admin” to something else would cause data import to fail. Now, you can rename the administrator account in an Identify tenant and use the Identify Configurator to successfully export or import data in this tenant.
Hangfire packages for MongoDB
This change only affects Identify tenants that use MongoDB for their Audit databases. The Hangfire packages have been updated for better compatibility and performance. They now include the latest MongoDB driver, enhancing system stability and resolving issues related to passwords containing special characters ($ : / ? # [ ] @ ,) when using them in the MongoDB connection string builder.
Full support for upgrading tenants using MariaDB
Identify tenants using MariaDB can now be fully upgraded from version 5.15 to the latest version.
OAuth 2.0 and OIDC
Identify 5.17 is a major release for OAuth 2.0 and OIDC. We have implemented several new profiles and added missing functionality to ensure full compliance with the already supported profiles.
Public clients and the ‘None’ option in the Token endpoint authentication method
The newly added Application type setting in OAuth/OIDC applications is used to guide the choice of authentication options. It does not determine whether a client secret is required at runtime; this is controlled by the Token endpoint authentication method setting. Additionally, we have implemented the None option in the Token endpoint authentication method setting, allowing your application to call the token endpoint without needing to authenticate.
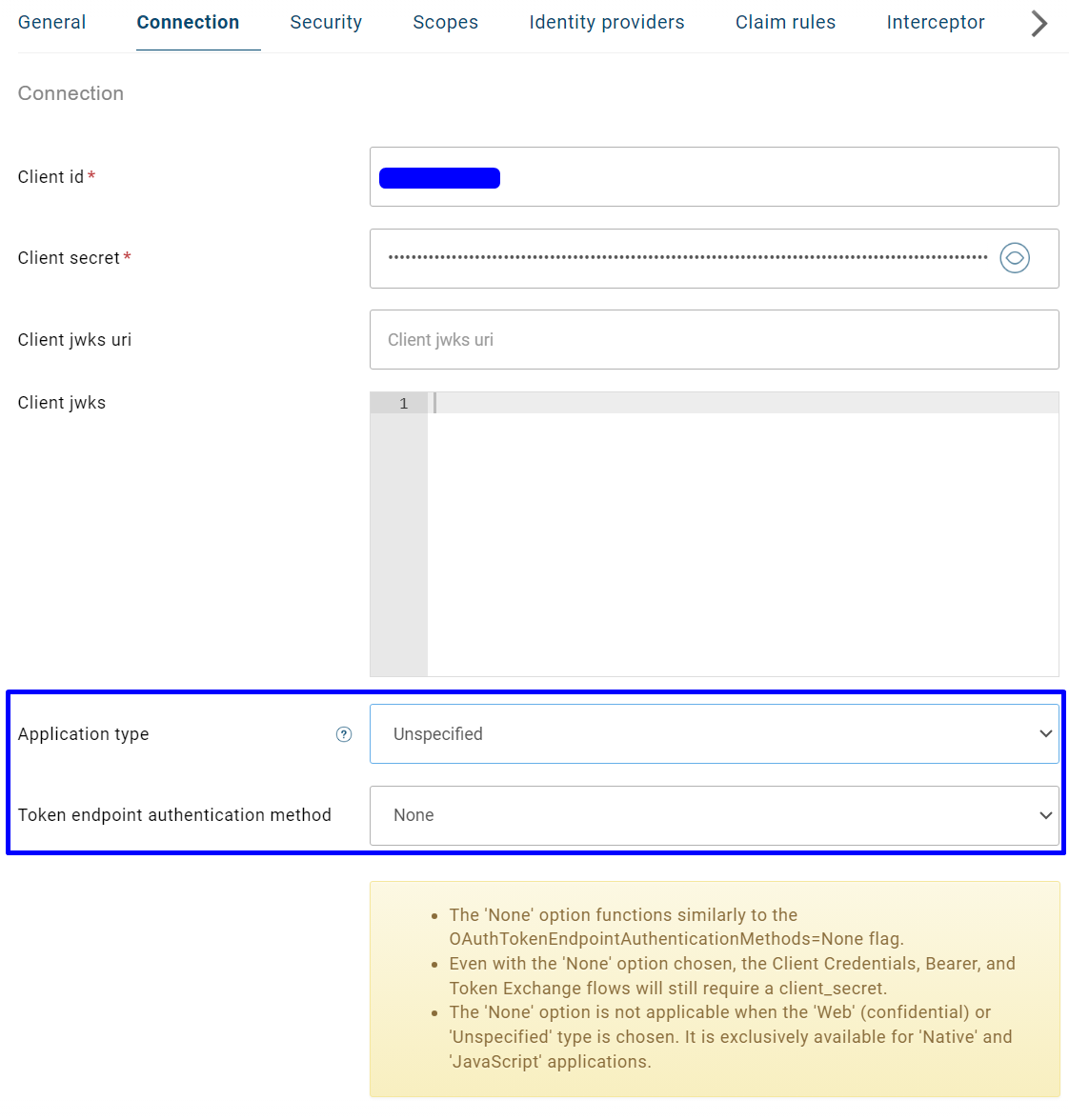
For more details, please refer to topic.
JSON Web Token (JWT) Profile for OAuth 2.0 Access Tokens
We have reviewed the JWT profile specification and made the following improvements:
- Updated the JWT Access Token header and data structure.
- Added support for the new resource parameter in both the authorization endpoint and the token endpoint.
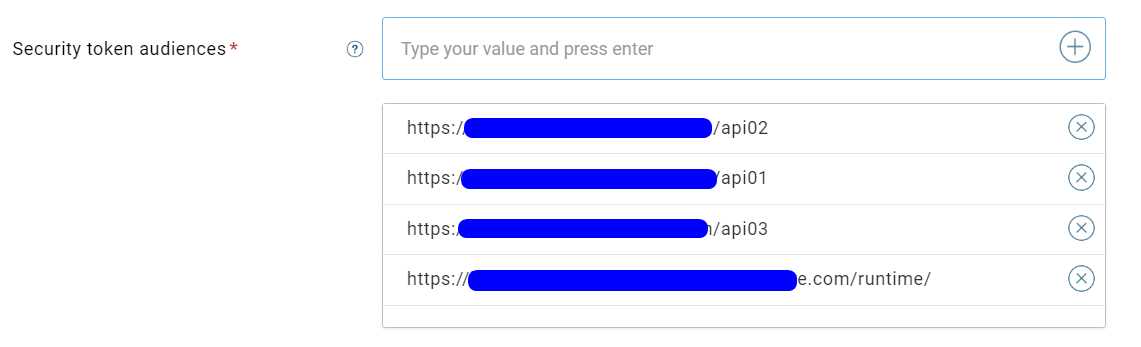
- Allowed input of a list of recipients for the Security token audiences setting. You now can use a single OAuth 2.0/OIDC connection to allow a client to access multiple resources, and the client can use the resource parameter to specify the specific resource it needs access to. Before this version, you had to create a separate OAuth 2.0/OIDC connection for each resource.
Mutual TLS client authentication and certificate-bound access tokens
We have implemented the RFC8705 profile OAuth 2.0 Mutual-TLS Client Authentication and Certificate-Bound Access Tokens. For more details on how to use this new feature, please refer to the documentation.
OAuth 2.0 token exchange
We have implemented the RFC8693 profile OAuth 2.0 Token Exchange, which allows you to implement the delegation/impersonation use case. For more details on how to use this new feature, please refer to the documentation.
Security enhancement
Identify now applies HTML encoding to input parameters when they are rendered in the OAuth error response to prevent potential reflected XSS attacks.
Upgrading components
We have upgraded the .NET version of Identify Admin and IdentifyMe to 8.0 and updated their dependencies. Similarly, most dependencies of Identify Runtime were updated, except for a few due to syntax and compatibility issues. Even if new dependencies do not introduce new features, upgrading them helps address security vulnerabilities found in older versions.
Identify Admin and IdentifyMe
Memory usage improvement for refresh token loading
We have improved memory usage when loading the refresh token list in Identify, especially on pages like the REST API key page. This enhancement aims to optimize performance by reducing memory consumption, resulting in faster load times and a smoother user experience.
Resource usage reports
We have added new resource usage reports within Safewhere Identify, such as an overview of users who have not logged in within a specified timeframe. Find more details on these resource reports:
Setting search across multiple tabs
The ability to search for settings across tabs is one of the most requested features, and we are now happy to finally ship it. This feature enables you to easily locate settings without needing to switch tabs, saving you time and effort. In this version, this function only works on the Identity providers, Applications, and Settings pages, which have so many settings spread across multiple tabs. Find more details on this topic.

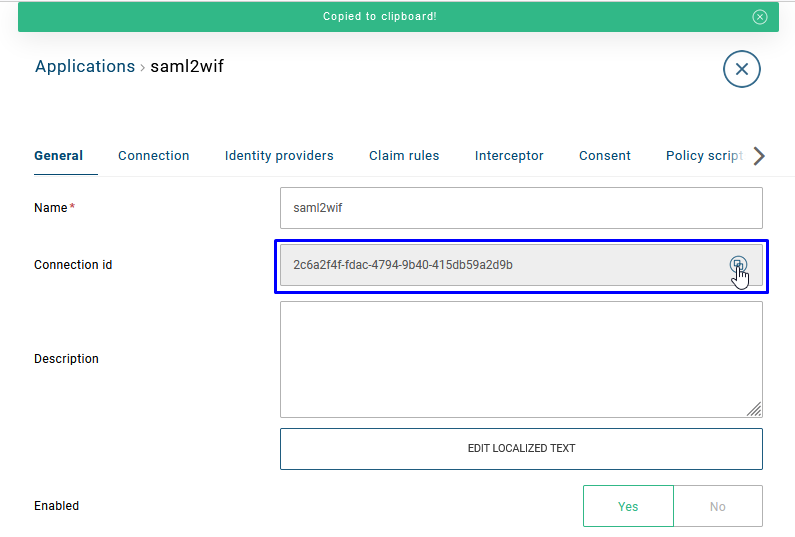
Resource ID display
We have added a new field to display the ID value of a resource for the following resource types:
- Users
- Claims
- Claim sets
- Claims transformations
- Groups
- Organizations
- Attribute service
- Clients
- Integrations
- Authentication context method class
- LDAP Web Services
- LDAP Attribute Definitions
There is also a Copy button that you can use to easily copy an ID for later use.
Ability to input Application Insight connection string
It is now possible to use either the Instrumentation Key or the full Connection string to configure logging to Application Insights. For more details, please refer to this topic.

Other improvements
Notify users about their OTP authenticator changes
We have documented a method for notifying users when their OTP methods change, specifically for OS2faktor, Email, and SMS.
Additionally, Identify has introduced some changes to the messages sent to the service bus when there are changes to user authenticators:
- Added DetailMessageType to MessageJson
- Using OtpTypeName instead of a numeric value
- Using OtpConnectionName instead of connection ID
You can find more details on this topic.
Improving onboard data validation when toggling “Encrypt secret code” on or off in an OTP connection
Toggling the Encrypt secret code in an OTP connection on or off after some users have onboarded may disrupt their authenticator data. When encryption is enabled (i.e., Encrypt secret code is set to ON), Identify will attempt to decrypt users’ secret keys during login, which can cause errors if the keys were not previously encrypted.
In this version, when the Encrypt secret code is set to ON, users who have already onboarded their data can continue logging in normally without disruption.
Resolving the issue of unknown UserId in logs
Logs of requests to the REST API now have the UserId property correctly set to the user ID value found in access tokens. Previously, it was incorrectly set to ‘Unknown’.
Breaking changes
When upgrading your Identify instance from a previous version, you might encounter some breaking changes:
Changes in Hosted forms
The following Hosted forms have been modified to implement HTML fixes:
- AuthenticationList
- RecoveryCode
- Error
- FirstFactorWebAuthnError
- IdentifyMeErrorPage
- OtpMalformedRequestError
- ReportError
- IdentifyMeEnableAuthenticator
Please refer to these PRs: 49 and 50 for more details about the changes.
Changes in Razor
The following Razor views have been modified to remove redundant title content:
- DeleteCookies
- LanguageChooser

The Error Razor view has been modified to ensure that the custom exceptions are recorded in the log content:

Other changes
- The typ header of issued access tokens in version 5.17 is “at+jwt”. To revert it back to JWT, add a setting called header_typ in the OAuth/OIDC application and set its value to JWT.

5.17 REST API change
You can find the new changes on 5.17 APIs here.
5.17 Known issues
You can find the known issues of version 5.17 here.
Bug fixes
- Fixed: #112919 [IdentifyAdmin] HTML errors in the hosted forms: Login, Error Page, Report Error, OTP Malformed Request Error, and First factor web authentication login error
- Fixed: #112885 [IdentifyAdmin] HTML errors in the RecoveryCode hosted form
- Fixed: #112750 [IdentifyAdmin] JavaScript error this.attributeService.metadataReference is null is logged when uploading attribute service metadata
- Fixed: #109287 [IdentifyAdmin] Typo in the WS-Federation application signout endpoint setting
- Fixed: #107303 [IdentifyAdmin] The message “Please be aware that skipping this step will result in the loss of all your previous work. Simply click the ‘Continue’ button to finish the process.” does not render in the preview mode of the Onboarding succeeded hosted form
- Fixed: #112511 [IdentifyAdmin] The application/identity provider content does not update when uploading the same metadata file more than once
- Fixed: #108789 [IdentifyAdmin] The selected organization in the owner organization section is not reset when choosing All locked users in the user list
- Fixed: #108201 [IdentifyAdmin] Error code 500 returned when deleting a claim in use by the LDAP claim transformation in the claim list
- Fixed: #108013 [IdentifyAdmin] Error message incorrectly displayed when OS2faktor method is not selected in OTP connection’s second factor methods
- Fixed: #108002 [IdentifyAdmin] Custom regular expression in the EmailAddress field configuration does not apply to email input validation
- Fixed: #107281 [IdentifyAdmin] User certificate removed after after correcting user information due to the error message: “Failed to proceed since you tried to set the email to
which has already been registered by another Identify user”. - Fixed: #107189 [IdentifyAdmin] The logged username information is URL encoded in the authenticator application when resetting his authenticator on the My Profile page
- Fixed: #107353 [IdentifyAdmin] Typo in text resource key in the GenericProviderResources file
- Fixed: #107511 [Swagger] Missing descriptions for Parameters and Validations in the ScriptLibrary resource
- Fixed: #109554 [RESTAPI][Users] Endpoint /admin/api/rest/v2/users/.filter incorrectly includes users who have not registered any value when searching for those who have registered any value in a specified claim type
- Fixed: #108586 [RESTAPI] Incorrect behavior when retrieving users with a negative pageSize parameter via
GET /rest/v2/users - Fixed: #108231 [RESTAPI] The length of the claim/claimset name can exceed 256 characters
- Fixed: #110082 [OAuth] Event IDs 4950 (SYS) and 4910 (SEC) are missing when an authorization request returns the error code invalid_scope
- Fixed: #112025 [OAuth] Recently added grant types are missing in the grant_types_supported key in the OpenID Connect Discovery endpoint
- Fixed: #110747 [OAuth] Error code 500 returned when the requested token endpoint includes
openidscope and an invalid grant type - Fixed: #108279 [OAuth][DevicePairing] Error response not returned when calling the token.idp with only device_code and client_id while the OAuth/OIDC application’s token method is set to clientsecretbasic
- Fixed: #109694 [Logging] Incorrect log level for the logged presenter claim in log content
- Fixed: #107736 [Logging] Event IDs added to the exclusion list in the previous logging filter rule are not excluded the newly applied logging filter rule does not include an exclusion rule
- Fixed: #107236 [Runtime] Redundant title content in the razor views: Language Chooser, Delete Cookies
- Fixed: #112535 [IC] Secrets are incorrectly handled when configuring the encryption key for the Identify database
- Fixed: #108018 [IC] Out-of-date zxcvbn-core library used in Identify configurator
- Fixed: #107045 [IC] An instance using MongoDB/CosmosDB as its audit provider encounters a failed deletion when executing the drop tables script in the IdentifyAudit database
- Fixed: #108192 [IdentifyMe] HTTP 400 error occurs immediately after pressing the Confirm button on the Authenticator page when using the IdentifyMeEnableAuthenticator hosted form
- Fixed: #107820 [OTP] Custom exception logging was not functioning when errors occurred on client machines




